xmlrpc.php allows SSRF!
During my recent bug bounty hunting journey, I encountered a potential SSRF (Server-Side Request Forgery) vulnerability in the xmlrpc.php file of the Wurth.es website. In this post, I will walk you through the vulnerability discovery process, its impact, and possible remediation steps.
What is xmlrpc.php?
The xmlrpc.php file in WordPress is used to enable remote communication between the website and external services. While this file serves legitimate purposes, it can also be exploited for malicious activity if improperly secured.
One particularly dangerous method within xmlrpc.php is the pingback.ping method, which allows interaction with external servers. Attackers can exploit this function to perform SSRF attacks, where they trick the vulnerable server into making requests to unintended destinations, leading to severe consequences.
Steps to Reproduce the Vulnerability
- Send request to https://example.com/blog/xmlrpc.php

2. Switch the request method from GET to POST and add the following xml code in the request body.

3. This will return a xml code that represents some methods like system.multicall, pingback.ping, metaWeblog.deletePost etc. Here some methods need authentication as admin. But I tried to use pingback.ping
4. Modify the request with following code:

Change the SERVER url with any server of your own. Here, I use BurpSuite Collaborator for this purpose. The request looks like:

Proof of Vulnerability:
The response of the above request looks like:
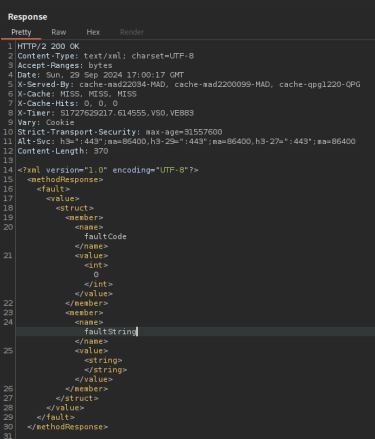
Just notice the Collaborator for POC….

You will see a request came in Collaborator server , that is the pinging request generated in the previous request. That proves that our our example.com is communicating with random servers!
No more today! Don’t ask about bounty! I like being victim of scams….









